
Table of contents
What are the file server security challenges?
-
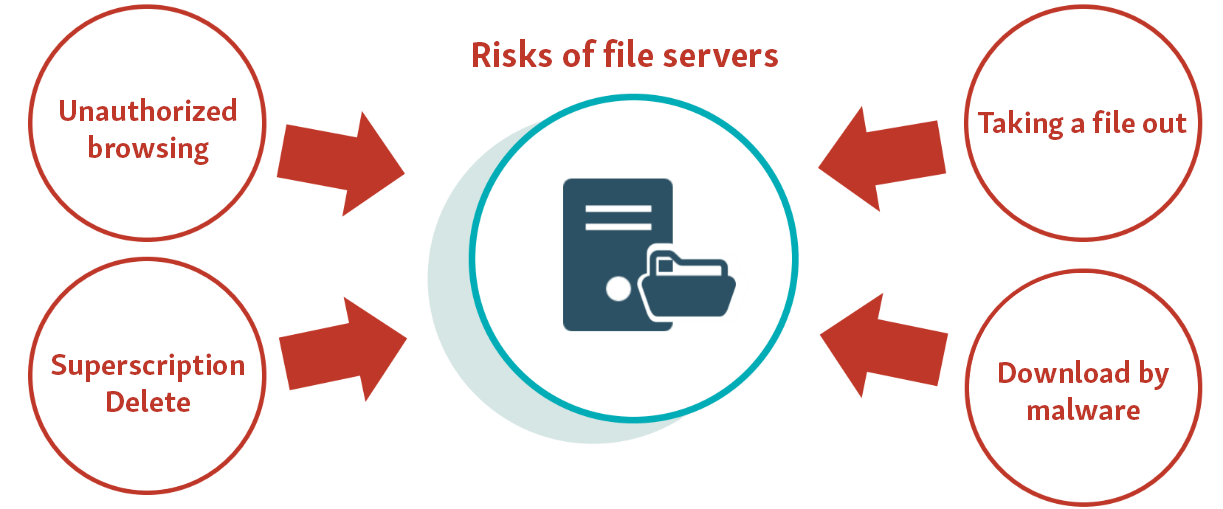
Risk of leakage of confidential information
Unauthorized access to a file server, which holds almost all of a company’s confidential information, is a serious incident that can cause information leaks.
-
Risk of information leakage by employees
There is a risk that removal of data by authorized employees may occur, whether intentionally or negligently.
-
Early response to incidents
In the event of an incident, early detection and early response are necessary to minimize damage.
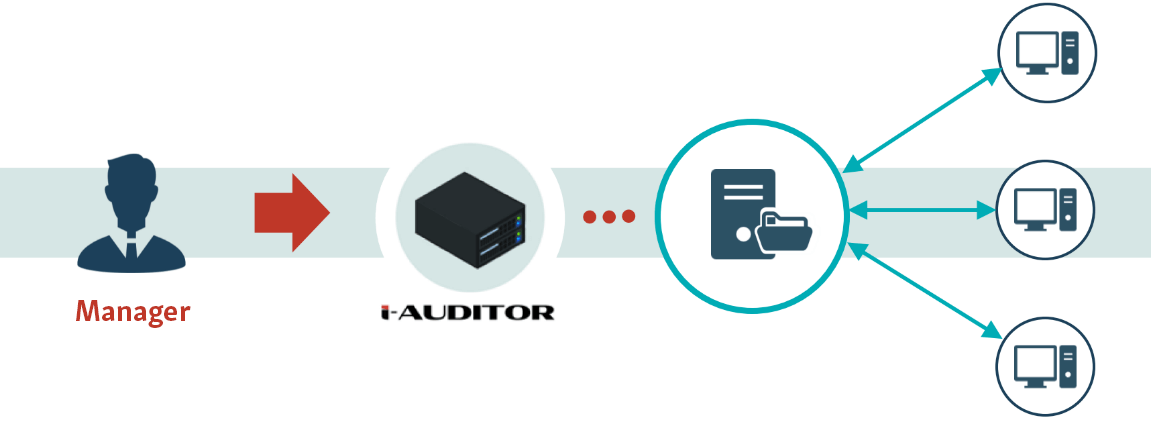
Overview of i-Auditor
i-Auditor is a network monitoring system specialized for monitoring access to file servers.
All file servers in the company can be centrally managed, and non-specialists can monitor and check logs.
What i-Auditor can do for you
-
Centralized management of access logs for the entire organization
Monitoring and analyzing logs is necessary to reduce the risks posed by file servers.
With i-Auditor, access logs to all file servers in the company can be centrally managed, viewed, and analyzed on-screen.
-
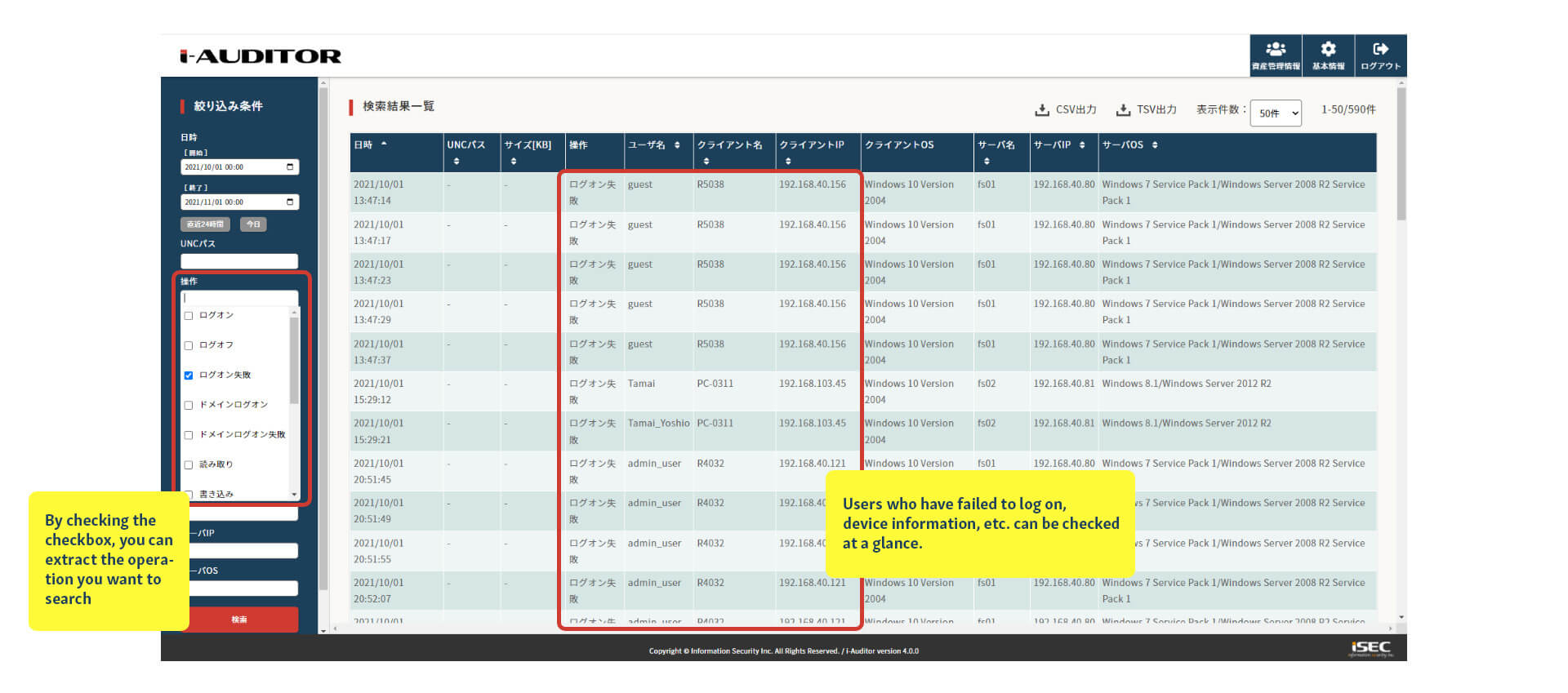
Visualization of access status and unauthorized access detection
From the administration screen, you can check for unauthorized access by specifying conditions and visualizing the status of access to the file server. For example, if a user fails to log on multiple times, signs of unauthorized access can be detected.
It is also possible to manage assets such as whether vulnerable terminals such as Windows 7 are being used.
-
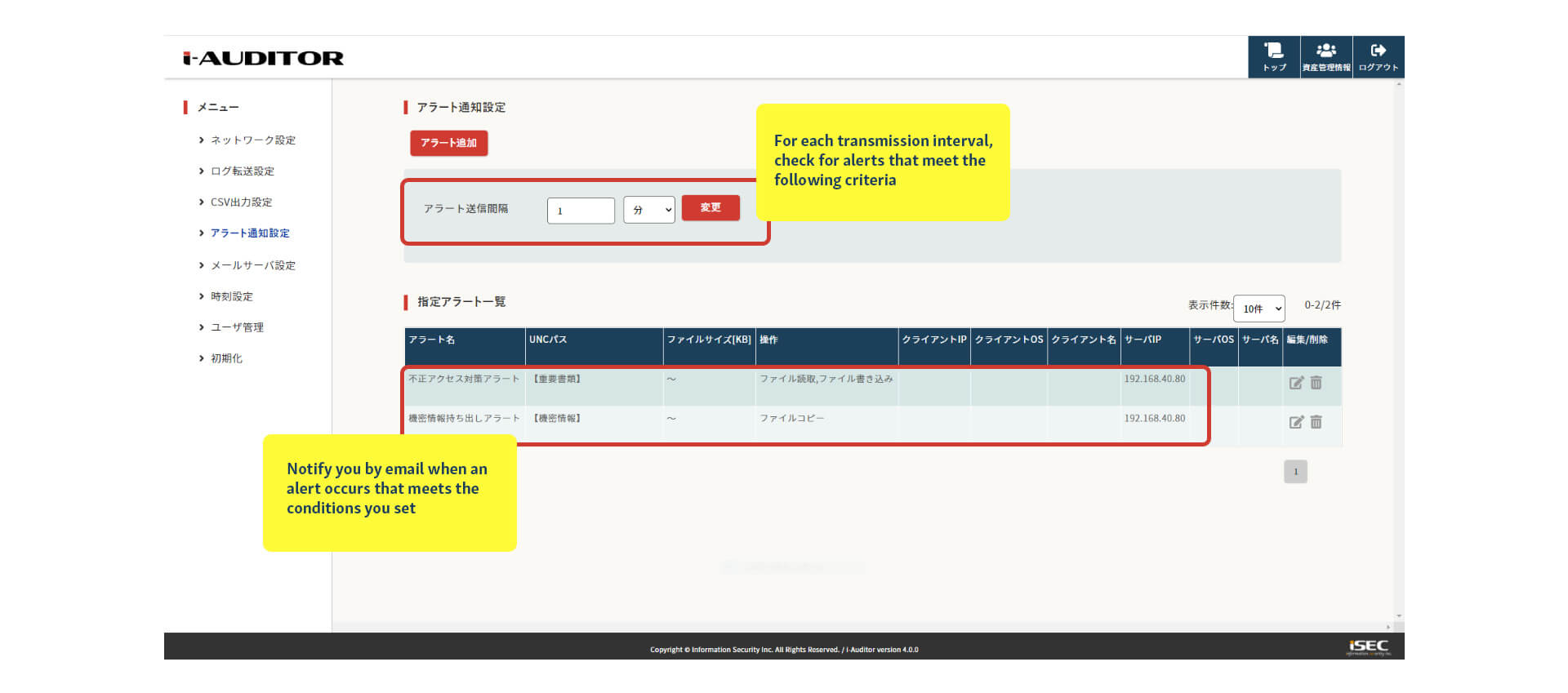
response to incidents with real-time alerts
By registering the conditions for detection in advance, you can receive notifications via e-mail when unauthorized access occurs. This enables early detection and early response to unauthorized access.
Why choose i-Auditor?
-
POINT 1: Excellent operability and functions to shorten survey time
The intuitive UI and the ability to identify and display only the necessary logs greatly reduces work time. When an incident occurs, a quick response is required to minimize damage. i-Auditor allows for quick investigation.
-
POINT 2: Can be installed on a wide variety of file servers
Support for standard protocols Kerberos and SMB allows for deployment on any OS, and supports all types of file servers, including TeraStation, NetApp, Equallogic, and ReadyNAS.
-
POINT 3: Speedy implementation
Because it collects data by capturing packets, it can be deployed quickly by simply connecting to a switch. No agents or other software need to be installed on each server or terminal, and there is no impact on the existing network when deployed.
Price
Purchase terms are in one-year increments. For more information, please click here to apply.
If you would like to receive more information about this product, please follow this link.
Frequently Asked Questions
-
How many users can you support?
As a rough estimate, we can handle up to 10,000 to 20,000 users.
-
Do I need to do any configuration for the server?
No need. No additional configuration is required.
-
How long does it take to implement?
If you prepare LAN cables for mirror acquisition in advance, installation can be completed in 30-60 minutes.
-
Is it possible to build i-Auditor on a virtual environment?
Yes, we distribute iSO images as a virtual version of i-Auditor.
